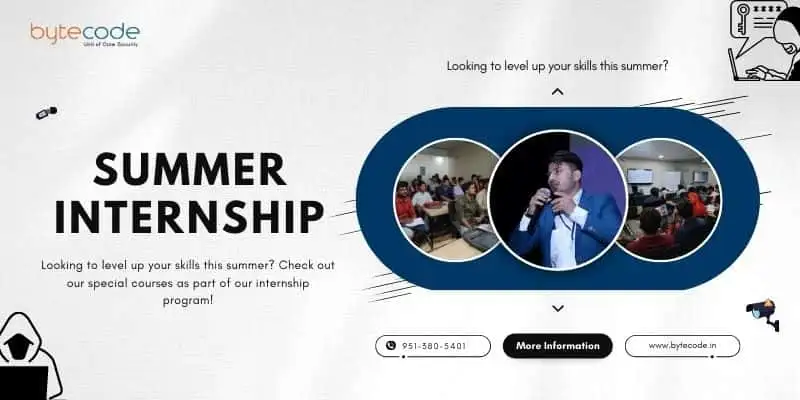
Penetration Testing Summer Internship in Delhi
internationally approved penetration testing Summer Internship course in Delhi is the best cybersecurity course you can join under the guidance of industry expert pen testers. We provide pen testing labs online and offline. The penetration testing process helps you to know vulnerabilities in your system whether in networks or web applications. Our penetration testing course in Delhi provides advanced network penetration testing techniques and attacks in real-world scenarios. Advanced Penetration Testing is also known as Pentest, There are a lot of penetration testing certifications like CPENT, ECSA, CEH, OSCP, and OSWP. You can go for these certifications after learning penetration testing at Our Institute.
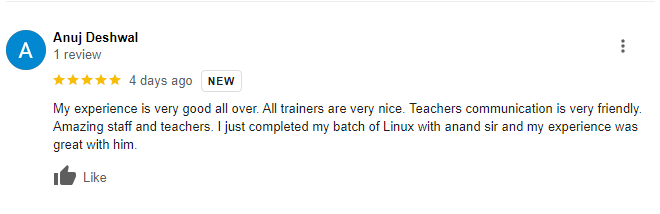
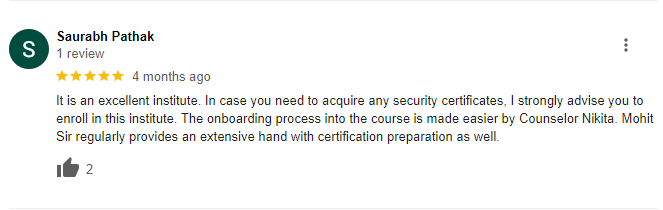
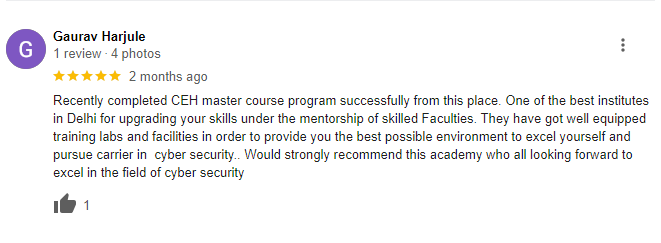
Bytecode Cyber Security Pvt. Ltd. is the right place to learn something new with the latest tools. Bytecode Cyber Security offers you a Penetration Testing summer internship in India. Penetration testing training is taught at Bytecode Cyber Security with experienced trainers. These courses provide real-world, hands-on practice sessions that are basically used in the cyber security field all over the world. Bytecode Cyber Security includes courses on cybersecurity and ethical hacking, penetration testing and security audits, network and data forensics, in-depth networking, and application security on various platforms. So you can learn a lot of cyber security and penetration testing courses, ethical hacking courses, network security, and web application security-related topics, and you can learn other programming languages like Java, PHP, and Python and learn a lot from their institute. It is a very nice place for students to learn about penetration testing courses and cyber security.
Eligibility Criteria For Penetration Testing Summer Internship
Any graduate, undergraduate, or post-graduate student having a passion for information security can undergo our Cyber Security course in Delhi and become a certified ethical hacker. If you are willing to know more about the course or admission eligibility, just give us a call and we will suggest the best batch option for you.
Learn From Home with Online Training
Bytecode Cyber Security Provide 24x7 Classes
Students can attend classes from their homes. It takes less time to attend an online class. At the same time, various groups can attend online classes with bytecode Cyber Security From home.