Online Mobile Application Security Summer Internship in Delhi
ABOUT THE ONLINE MOBILE APPLICATION SUMMER INTERNSHIP
Mobile application Summer Internship become an essential part of our lives as our dependence on our smartphones has grown and to secure them are a crucial requirement because Mobile application carry your data information in many forms. Penetration Testing can provide us with a certain level of confidence, but hacking into Mobile applications Summer Internship demands a different approach and setup than with web applications.
We Provide Cyber Security Training to our students, Corporate clients, and partners because we believe that the high standards bring excellent output. We prepare our students how will they secure at our end from Malware and viruses. Our clients learn Ethical Hacking, Cyber Forensics, Networking, and some security courses in bytecode cybersecurity for becoming Security Analysts.
Learn From Home with Online Training
Bytecode Cyber Security Provide 24x7 Classes
Students can attend classes from their homes. It takes less time to attend an online class. At the same time, various groups can attend online classes with bytecode Cyber Security From home.
Eligibility Criteria
Any graduate, undergraduate or post-graduate student having a passion for information security can undergo our Cyber Security course in Delhi and become a certified ethical hacker. If you are willing to know more about the course or admission eligibility, just give us a call and we will suggest the best batch option for you.
Mobile Application Security Summer Internship Curriculum
Module 02: Insecure Data Storage
Module 03: Insecure Communication
Module 04: Insecure Authentication
Module 05: Insufficient Cryptography
Module 06: Insecure Authorization
Module 07: Client Code Quality
Module 08: Trojan and Back door
Module 09: Code tempering
Module 10: Reverse Engineering
Module 11: Extraneous Functionality
Our Students Placed in Companies




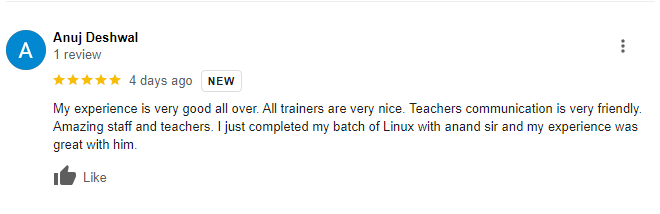
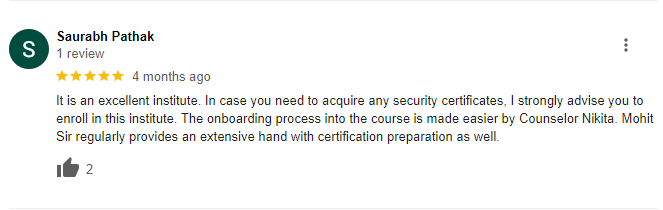
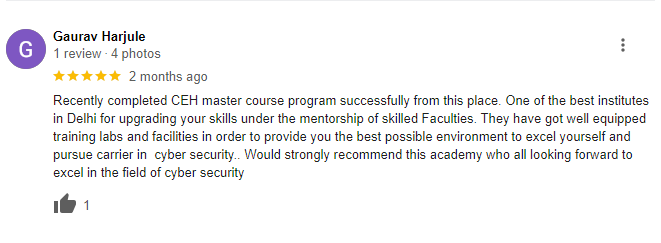
Our Google Reviews
Our Related Course
Frequently Asked Questions
About The Mobile Application Security Training Course Program
What are the security techniques in mobile applications?
The current study describes the primary security techniques used in primetime mobile applications, including the following:
- Encryption
- Secure Storage
- Authentication
- Access Control
- System Updates
- Secure Network Communication
What are examples of application security?
The primary instances of application security are outlined below:
- Authentication and Authorization
- Data Encryption
- Firewalls
- Secure Socket Layer (SSL)
- Intrusion DetectionApplication Patching
- Access Controls
- Identity and Access Management (IAM)
- Security Testing
- Web Application Firewall (WAF)
What are the risk in mobile applications?
People encounter a variety of risks when using mobile applications, which they must learn to avoid during a mobile application security course. The following list lists a number of notable risks related to mobile applications:
- Insecure Communication,
- Lack of Input Validation,
- Insecure Data Storage,
- Client Code Security,
- Insufficient Authentication and Authorization Controls,
- Poor Encryption,
- Reverse Engineering, etc.
You can enroll in Bytecode Security's top-notch Mobile Application Security Course in Delhi NCR, which is led by highly qualified and experienced training mentors with years of excellent experience in the same trade if you want to learn more about the same topic. For other information about the same genre, give +91-9513805401 a call.
How hackers hack mobile apps?
Mobile applications frequently have security flaws that attackers find and take advantage of long before security professionals do. Then, these weaknesses are taken advantage of by applying tried-and-true methods, tools, and algorithms. As a result, hackers compromise mobile apps with the goal of taking advantage of their weaknesses for their own gain, which frequently results in significant financial losses for the owners of the apps as well as, in certain situations, the users.
How does Mobile Application Security work?
In order to protect mobile applications from potential hackers who might use malevolent methods to breach their security, penetration testing is carried out by competent and experienced mobile application security specialists.
Vulnerabilities can be checked not only in mobile applications but also in other IT infrastructures. We advise you to join the mobile application security course provided by the prestigious Bytecode Security facilities, which are situated at its institutional locations in Saket and Laxmi Nagar if you are interested in learning this information. Give +91-9513805401 a call to learn more.
What is attacks on mobile applications?
A group of programs or commands used by a malevolent actor or entity with the goal of gaining unauthorized access to another person's mobile application is referred to as a mobile application attack. Making illicit financial gains is the main goal of these attacks.
How much are mobile application security courses?
Popular mobile application security courses usually cost between ₹15,000 and ₹20,000 in India. However, there aren't many institutions that actually give genuine financial support to those from underprivileged and marginalized socioeconomic backgrounds. In the same spirit, Bytecode Security is helping students legitimately by offering thorough training on mobile application security.
Is Mobile Application Security course difficult?
The entry-level training mobile application course is available without charge and doesn't require any prior understanding of programming languages or the fundamentals of Linux. However, when students progressed through the more complex sections of the mobile application security course, there was a real need to increase their level of coding and Linux knowledge. Thus, as the course progressed, the level of difficulty increased.
What is the Mobile device threat?
Mobile App Threats and Mobile Device Threats are the flaws in the configurations of vulnerabilities, gaps, and threats. These can be found and eliminated with the help of specialized Penetration Testing techniques used by a qualified Pentester.
On the other hand, it is feasible for a malicious party to obtain unapproved access to and utilize the private datasets contained in the aforementioned mobile application for their own benefit.
What is application security and its types?
The term “Application Security” describes the methodical controls put in place to protect data and apps against breaches or unauthorized access. The extensive collection of security measures consists of several elements, such as software patching, authentication, authorization, and encryption, all of which are designed with the express purpose of protecting the functioning and integrity of application data.
Furthermore, the most common types of application security fall under the following categories:
- Access control
- Authentication
- Data encryption
- Application patching
- Network security
Why mobile application security is important?
In today's technologically advanced world, where the majority of users' databases are kept within mobile applications on their smartphones, it is undoubtedly possible to hack users' data using various hacking tools, methods, and techniques, and then use the information for personal gain. Therefore, it should be our first responsibility to ensure that the security of mobile applications is our top priority.
What do you mean by mobile security?
By applying a few tools, strategies, and procedures, a well-trained working professional can uncover hidden vulnerabilities, threats, and flaws in mobile applications that could be used by hackers in the future. This process is known as mobile application pentesting. In the same vein, anyone interested in completing this fantastic mobile application security course near Delhi NCR can apply to Bytecode Security's educational institutions in Saket and Laxmi Nagar.
How does mobile security work?
In order to identify the related to vulnerabilities, threats, and loopholes within the app that could be used by a malicious actor or entity for their own potential benefits, Mobile App Security conducts a series of attacks on the mobile applications with the owner's documented consent.
If someone is interested in learning more about offline and online mobile application security courses around Delhi NCR, they can get in touch with the top-notch Bytecode Cyber Security Institute facilities at its branches in Saket and Laxmi Nagar.
What is the mobile device threat?
A mobile device threat is defined as a programming error that occurs during the careful development of a mobile application. A malevolent actor can identify, follow, and take advantage of this kind of threat or weakness by employing some of the unique tools, ploys, and methods.
By enrolling in and completing an excellent mobile application security course from a real teaching expert, such as those at the Bytecode Cyber Security Institute's Saket and Laxmi Nagar branches, one can also protect themselves against these kinds of dangers or vulnerabilities.
How much are mobile application security courses?
Normally, the cost of the Mobile Application Security education is from ₹15,000 to ₹20,000; however, the Bytecode Cyber Security Institute provides this excellent education at incredibly affordable rates. A knowledgeable educational counselor can answer questions regarding the same by contacting our helpline at +91-9513805401 on a mobile device.
Is mobile application security course difficult?
We can say with certainty that the mobile application security course is challenging because it requires a good grasp of coding and programming languages. Learning multiple programming languages, such as C, C++, Java, Python, and so on, is necessary to work well with mobile application security solutions. In addition, it's important to have a solid understanding of the fundamental commands in Linux.
Can you pen test a mobile app?
You can really pentest a mobile application after fully understanding all of the course's foundational material. Therefore, you can enroll in a real Mobile Application Pentesting Security Course offered by Bytecode Security if you truly want to pentest a mobile application in its entirety.
How to test security testing in mobile application?
To determine whether a mobile application is sufficiently protected against potential attacks and vulnerabilities, security testing must be implemented. Because mobile apps handle sensitive data on a regular basis—from financial information to personal user information — it is imperative that their security be guaranteed. This document provides thorough instructions on how to test mobile applications for security:
- Understand the Mobile Ecosystem,
- Set Up a Testing Environment,
- Information Gathering,
- Data Storage and Privacy Testing,
- Input Validation Testing,
- Session Handling,
- Authentication and Authorization Testing,
- Intercepting Network Traffic,
- Client-Side Injection,
- Test for Malware,
- Check Code Security,
- Third-party Library Testing,
- Physical Security Testing,
- Use Automated Tools,
- Post-release Updates and Patches, etc.
How much does mobile app pen testing cost?
Bytecode Security's Mobile Application Security Course is very competitively priced, and it's hard to locate a comparable course in this price range in the present market conditions. However, all you have to do to speak with one of our incredibly knowledgeable educational counselors is to give us a call at our hotline mobile number, +91-9513805401.
What is the cost of Pentesting in India?
The cost of Pentesting in India depends on the various functionalities. However, we have jotted down some of the mainstream costings in the below table:
| Basic automated vulnerability scans | Might range from INR 10,000 to INR 50,000. |
| Standard web application or mobile application pentest | Can vary from INR 50,000 to INR 3,00,000 depending on the complexity and depth. |
| Comprehensive assessments, including Red Teaming | These can range from INR 5,00,000 to INR 15,00,000 or even more, depending on the project's scope and the service provider's stature. |
Are pen testers in demand?
There is a high demand for penetration testers, also known as pen testers, at the moment. In the modern cybersecurity landscape, their role in identifying and addressing vulnerabilities in systems, networks, and applications is critical.
What is the salary of a Pentester in India?
The salary of a pentester in India is mentioned below”
- Entry-Level (0-2 years of experience): INR 3,00,000 to INR 7,00,000 per annum.
- Mid-Level (3-6 years of experience): INR 8,00,000 to INR 15,00,000 per annum.
- Senior-Level (7+ years of experience): INR 16,00,000 to INR 30,00,000 or more per annum.
How much does AWS pentest cost?
The process of conducting penetration testing on Amazon Web Services (AWS) environments encompasses the assessment of the security measures implemented on the cloud infrastructure, applications, and configurations that have been deployed on the AWS platform. The cost of penetration tests might fluctuate depending on a variety of factors.
Moreover, the estimated figures for the cost of AWS Pentest is mentioned below:
- The cost of conducting rudimentary automated vulnerability assessments might vary between $1,000 and $5,000.
- The cost of comprehensive AWS pentesting engagements might exhibit significant variation, ranging from $5,000 to $50,000 or even higher, contingent upon the aforementioned considerations.
How much do pen tester hackers make?
In India, the penetration testers make around an amount of ₹18,19,269/-
Which type of hacker is highly paid?
Popularity-wise, network administration, Linux competence, cybersecurity know-how, IT infrastructure understanding, and security experience are the skills that ethical hackers find most appealing. For ethical hackers, the skill set of network security management is quite profitable since it pays 59% more than the average income scale.
What is the highest pentester salary?
For a penetration tester, the highest income possible is ₹18.4 Lakhs per year, or ₹1.5 Lakhs per month. What is the connection between penetration tester pay in India and experience? An entry-level penetration tester with less than three years of expertise in the field often makes ₹4.8 lakhs a year on average.