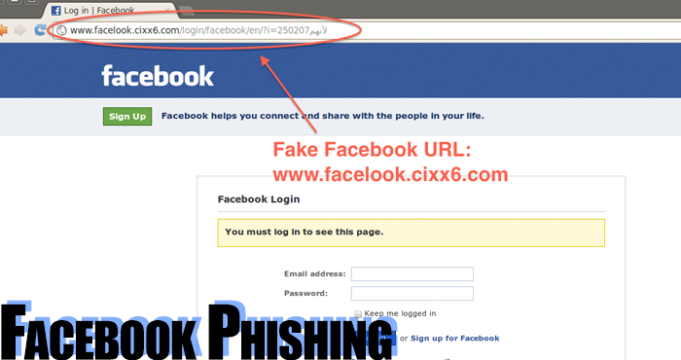
Learn Ethical Hacking and Facebook Hacking Course at Bytecode Security To make a Facebook phishing page, we use the Zphisher tool. To download the Zphisher tool types git clone https://github.com/htr-tech/zphisher.git then type cd/zphisher ./zphisher Type 1 because we are making… Read More