About Six Month Diploma in Information Security Summer Internship in Delhi, NCR
In this COVID-19 situation, bytecode provides you with a short-term “6 Month Diploma in Information Security Summer Internship “Course. You can learn from home we provide “online classes” as per your schedule because bytecode cybersecurity provides online training 24×7. So it is easier to get more knowledge from online classes at home. Students will get a live class video of their course after completion.
Summer Internship in Diploma in Information Security Specialization by Bytecode Cyber Security is a new 6-month diploma course with a 100% job guarantee. We have especially designed this course for students who want to excel in a career in cybersecurity. In this, we tend to cover the most industry-demanded areas, considering international industry-oriented courses, making an exclusive pack of one combo. The exposure to practical learning is very high. You will get a huge amount of time to practice using live projects and real-time simulations to become an expert in cybersecurity. Cybersecurity has become one of the most required fields in IT and with this, the sector is booming with jobs. We have been in the industry for a long time and have experienced faculty who impart theoretical knowledge with practical,, hands-on experience. Our Expert diploma course in cybersecurity will give you a chance to make a great career in the field of cybersecurity.
We only deliver the best quality and knowledge base solutions with a very high standard to our students, clients, and partners because we believe that high standards bring excellent output in the long run, Our standards are our strength, and we support these standards so that when we say “We are Professional in It,” we really mean it.
We provide Cyber Security Summer Internship Training to our students, corporate clients, and partners because we believe that high standards bring excellent output. We teach our students how be secure at our end from malware and viruses. Our clients learn ethical hacking, cyber forensics, networking, and some security courses in bytecode cybersecurity for becoming security analysts. Bytecode launched a Master’s Diploma, which includes 12 special training courses from basic to advanced levels to become an expert in cyber security, under the guidance of Mr. Mohit Yadav.
DOWNLOAD SIX MONTH DIPLOMA in INFORMATION SECURITY PDF – Click Here to Download
This bundle takes these popular courses and conveniently packages them into a single price with huge savings. This Bundle includes the following courses which are given below kindly check these courses :
Ethical Hacking
Ethical Hacking Security Experts have designed an Ethical Hacking course Training & Certification Program in Delhi, Laxmi Nagar, Rohini to meet real-world Ethical Hacking scenarios to help students and Corporate to perform similar Cyber Security Vulnerability Testings on their Networks and Web applications. In addition, this ethical hacking course will provide you certification for Beginners and intermediate levels. It includes more than 2200 Ethical Hacking tools and more than a hundred practicals which will give you all ethical hacking information.
- Introduction to Basics of Ethical Hacking
- Foot-printing Active (Tool Based Practical)
- Foot-printing Passive (Passive Approach)
- In-depth Network Scanning
- Enumeration User Identification
- System Hacking Password Cracking & Bypassing
- Viruses and Worms
- Trojan and Back door
- Bots and Botnets
- Sniffers MITM with Kali
- Sniffers MITM with Windows
- Social Engineering Techniques Theoretical Approach
- Social Engineering Toolkit Practical Based Approach
- Denial of Service DOS & DDOS Attacks
- Web Session Hijacking
- SQL Injection Manual Testing
- SQL Injection Automated Tool Based Testing
- Basics of Web App Security
- Hacking Web servers Server Rooting
- Hacking Wireless Networks Manual CLI Based
- Hacking Wireless Network
- Evading IDS, Firewall
- Honey pots
- Buffer Overflow
- Cryptography
- Penetration Testing: Basics
- Mobile Hacking
- Internet of Things (IOT) Hacking
- Cloud Security and many more
View Course Details | Book Your Seat | Download Course Content
Advanced Penetration Testing
Penetration Testing course is a purely real hardcore Practical based Penetration testing Process to test the Network, web application, thick client, mobile application, IoT devices, and much more. It is an advanced course that comes straight after Ethical hacking level one and it will go deeply till exploitation.
- How to Plan Your penetration Testing
- Scoping your penetration testing
- Network and Web Application
- Post Exploitation Phase
- In Depth Password Attacks
- Web Application Penetration Testing
- Penetration test Report
View Course Details | Book Your Seat | Download Course Content
Cyber Forensics Investigation
Cyber Forensics Investigation course include the following problems like the mishandling of confidential data, violation of intellectual property rights, trade secrets stealing, and other types of online fraud. In cyber forensics investigation, investigator uses different kinds of methods and techniques for faster case resolution.
- What is Computer Forensics
- Methods by which Computer gets Hacked
- Methods by which Computer gets Hacked
- Digital Evidence Gathering
- Computer Forensics Lab
- Setting up Forensics Lab
- Understanding Hard Disk
- File Systems Analysis : Linux/Window/mac
- Windows File Systems forensics
- Data Acquisition Tools and techniques
- Data Imaging Techniques and Tools
- Recovery Deleted Files and Folders
- Deleted Partitions Recovery Technique
- Forensics Investigations Using Forensics Toolkit (FTK)
- Forensics Investigations Using Forensics Toolkit (Oxygen)
- Forensics Investigations Using Encase Tool
- Stenography and Image File Forensics
- Application Password Crackers
- Log Computing and Event Correlation
- Network Forensics Tools : Cellebrite Tool
- Investigating Tools
- Investigating Network Traffic : Wireshark
- Investigating Wireless Attacks
- Investigating Web Application Attacks via Logs
- Tracking and Investigating Various Email Crimes
- Detailed Investiave Report
View Course Details | Book Your Seat | Download Course Content
In-Depth Advanced Networking
This course includes learning the CCNA basic concepts, the concept of layering in a computer network, and dynamic routing protocols. An in-depth networking training course deals with IPv4 and IPv6 networks and OSPF. In other words, Online Advanced Networking Course gives knowledge of Spanning Tree Protocol (STP) and Rapid Spanning Tree Protocol (RSTP).
- Introduction to Networking
- OSI Model
- TCP/IP Model
- Subnetting/Summarisation
- Packet Flow in Same & Different Network
- Information About Networking Device
- IP/ICMP
- APIPA
- ARP
- Routing Protocols(Static & Dynamic)
- Static : Next hop/Exit Interface
- Dynamic : RIP/EIGRP/OSPF & BGP
- Wan Technologies
- NAT
- ACL
- Dynamic Host Configuration Protocol
- Telnet & SSH
- Load Balancing Protocol
- Layers 2 Protocols
- VLAN
- Different Types of STP
- Ether Channel (L2)
- Port Security
View Course Details | Book Your Seat | Download Course Content
Web Application Security
This course will help students to get an instant job in Cyber Security. This course will brief you about the Security challenges in Web Application Security and the Security needed in Web Applications. This course will make you understand finding in Web Application and also about removing these Vulnerabilities Web Application.
- SQL Injection Flaws
- Cross Site Scripting Flaw
- Cross Code Disclosure Flaw
- OS Command Injection flow
- Broken Authentication
- File Upload Vulnerability
- Cross Site request Forgery
- Sensitive Data Explosure
- Remote File Inclusion
- Directory Traversal Attacks
- Invalid Traversal Flow
- Security Misconfiguration
- Missing Authentication
- Session Fixation
- Weak data Encryption
- Information Leakage
- Dangerous File Upload
- Invalid URL Redirection Flow
- Insecure Direct Object Reference
View Course Details | Book Your Seat | Download Course Content
Mobile Application Security
The mobile application has become an essential part of our lives as our dependence on our smartphones has grown and to secure them is a crucial requirement. Penetration Testing can provide us with a certain level of confidence, but hacking into mobile applications demands a different approach and setup than with Web Applications.
- Improper Platform Usage
- Insecure Data Storage
- Insecure Communication
- Insecure Authentication
- Insufficient Cryptography
- Insecure Authorization
- Client Code Quality
- Code Tampering
- Reverse Engineering
- Extraneous Functionality
View Course Details | Book Your Seat |Download Course Content
Python Programming
This Python Course will likewise enable you to ace significant Python Programming ideas for example- Information Activities, Document Tasks. Object- situated programming and different Python Libraries for example- Pandas. Which are fundamental for Data Science. For, basic and advanced python training in Delhi you have to find the best of the industries, and Bytecode Cyber Security is known for its best training, certified trainers, and assistance.
- Python - An Introduction
- Comparisons of Python with Other Language
- Python Variables & Data Types
- Operators
- Python Conditional Statements
- Python Looping Concept
- Python Control Statements
- Python Data Type Casting
- Python Number
- Python String
- Python List
- Python Tuple
- Python Dictionary
- Python Array
- Python Date & Time
- File Handling (Input / Output)
- Multithreading
- Python Mail Sending Program
- Database Connection
- OOPs Concepts
- Interacting with Networks
- Graphical User Interface
- Python Web Scraping
- Python for Image Processing
- Intro with Python Machine Learning
- Intro with Python Artificial Intelligence
View Course Details | Book Your Seat | Download Course Content
Who this Information Security Diploma Summer Internship Training course is for :
- Security Enthusiasts can pursue mobile application security courses.
- Any IT professional who wants to learn mobile security.
- Employees and college students can pursue this security course.
- Mobile Application Developers who want to understand mobile application security
- Security Administrators and IT Managers.
Our Students are Placed in Companies




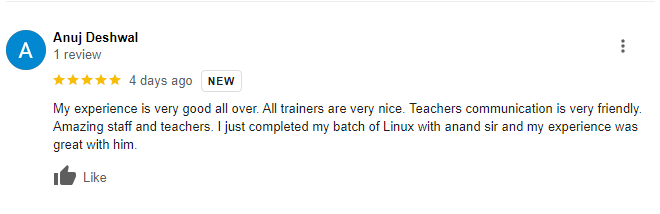
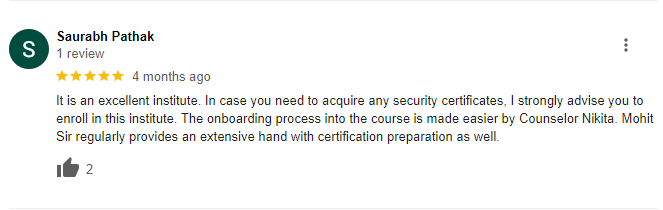
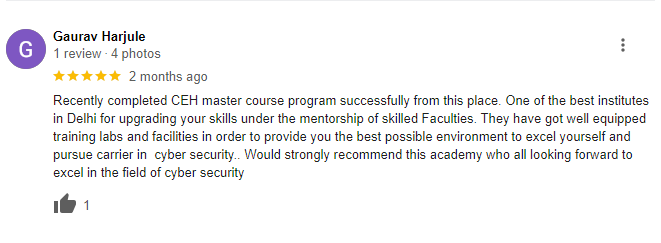
Our Google Reviews
Frequently Asked Questions
Can I do cyber security in diploma?
Yes, you can do a 6 Months Diploma in Information Security Course by Bytecode Security, the Best Cybersecurity Training Institute in Delhi.
What do you study in information security?
You will need to learn a number of topics in information security and develop your talents to the best of your abilities. However, the following are the key lessons you will learn from it:
- How to protect computer operating systems
- Ways to protect networks from unauthorized access
- Secure your data from cyber-attacks and many more.
How long is a diploma in cyber security?
The diploma in cyber security duration is 280 Hours, and in a month, it 6-month approx. It is provided by Bytecode Security.
What is Information Security courses?
Information Security courses are calculated and customized to offer knowledge about information security theories, practices, and objectives to several aspirants. Students looking for the best course related to information security can join a 6 Months Diploma in Information Security Course in Delhi offered by Bytecode.
For more information, contact Bytecode Security at its hotline number +91-9513805401.
Is information security a good career?
Since there are a number of data breach incidents happening all over the world, choosing information security as a career can be beneficial and lucrative. To know more about the same, give us a call at +91-9513805401.
How do I learn information security?
To learn about information security, there are several ways available in the international market. Some of them are - YouTube Videos, e-books, Books, PDFs available on online forums, Courses, etc.
But the best way you can learn such skills professionally is that you should join a 6 Months Diploma in Information Security Course in Delhi offered by Bytecode. This course is specially customized to offer a brief introduction to the needed information related to information security.
What are the 3 principles of information security?
The three principles that information security follows are as follows:
- Confidentiality
- Integrity
- Availability
What is the qualification for information security?
You should have some knowledge of computer science and information security with some programming skills. These are optional in the case of Bytecode. That’s because Bytecode has been introducing information security knowledge to several students for a long time and can teach you with professionals in their respective fields.
Even if you’re a 12th-passed student, you can learn it with Bytecode. In case you have some skills in a computer language, that would be great for your learning speed.
What are the three types of security?
The three types of security organizations need from professionals are:
- Management Security
- Operational Security
- Physical Security Controls