Online Web Application Vulnerability Summer Internship in Delhi
WEBAPP SECURITY Summer Internship (DIS Top 20 Critical Web Application Vulnerabilities) course will help candidates get deep information about the web applications security process. Web application security includes various vulnerabilities like SQL injection, PHP injection, XSS, CSRF, indirect object reference, and many more. This course will help students get instant jobs in Cyber Security. (25 Credits towards DIS10 Diploma)
Penetration Testing and Security audits, network and data Forensics, In-depth Networking, and Application Security on various platforms. These Courses are Highly preferred by Government Employees from various Intelligence Agencies. In addition to top-notch training, we also provide you with the best Industry Course Material Specially designed by DIS Master Consultants. DIS features top Industry Certifications in the Field of Cyber Security and Cyber Intelligence.
Students can attend classes from their homes. It takes less time to attend an online class. At the same time, various groups can attend online classes with bytecode Cyber Security From home.
Eligibility Criteria
Any graduate, undergraduate, or post-graduate student with a passion for information security can undergo our Cyber Security course in Delhi and become a certified ethical hacker. If you are willing to know more about the course or admission eligibility, just give us a call and we will suggest the best batch option for you.
DOWNLOAD WEB APPLICATION VULNERABILITY PDF – Click Here to Download
Web Application Vulnerability Summer Internship Curriculum
Module 02: Cross-Site Scripting Flaw
Module 03: Source Code Disclosure Flaw
Module 04: OS Command Injection Flaw
Module 05: Broken Authentication and Session Management
Module 06: File Upload Vulnerability
Module 07: CSRF – Cross-Site Request Forgery
Module 08: Sensitive Data Exposure
Module 09: Insecure Direct Object Reference
Module 10: Local File Inclusion and Remote File Inclusion(LFI and RFI attack)
Module 11: Directory Traversal Attack
Module 12: Insecure Transport Level Communication
Module 13: Information Exposure Through an Error Message
Module 14: Invalid URL Redirection Flaw
Module 15: Hard-coded Credentials in Static Code
Module 16: Hard-coded Credentials in Static Code
Module 17: Security Mis-Configuration
Module 18: Missing Authorization and Authentication for Critical Functions
Module 19: Session Fixation
Module 20: Weak Data Encryption
Module 21: Information Leakage
Our Students Placed in Companies




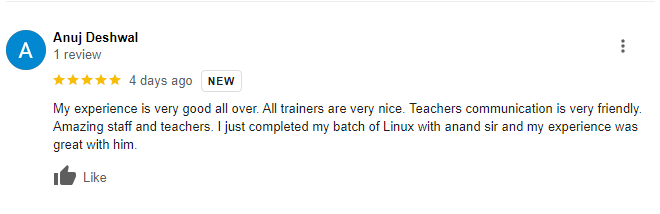
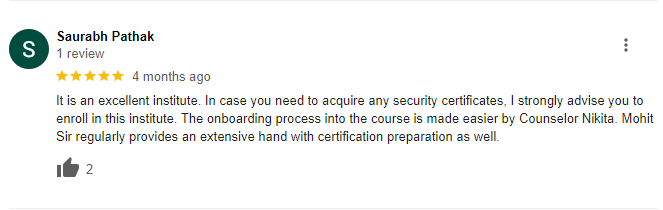
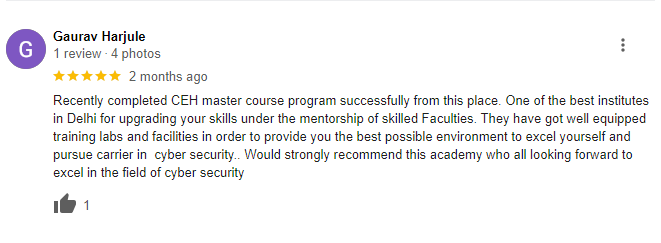
Our Google Reviews
Our Related Course
Frequently Asked Questions
About The Web Application Security Training Course Program
What are the top 5 Owasp Web vulnerabilities?
1) Injection.
2) Broken authentication.
3) Sensitive data exposure.
4) XML external entities (XXE)
5) Broken access control.
Why is Owasp important?
The OWASP Top 10 is important because it gives organisations a priority over which risks to focus on and helps them understand, identify, mitigate, and fix vulnerabilities in their technology. Each identified risk is prioritised according to prevalence, detectability, impact and exploitability.
What is Web application attack?
Upon identifying the vulnerabilities, dangers, and loopholes present in a web application, an individual with malicious intent proceeds to execute a sequence of coding attacks specifically targeting that web program. This type of attack is sometimes referred to as a web application attack.
In case you want to learn more about Web Application Attacks, you can join a prominent Web Application Security Course in the online or offline version by Bytecode Security, where you will get highly qualified training mentors. Call +91-9513805401 to know more.
What is SQL Query Injection?
SQL Query Injection, also referred to as SQLI, is a prevalent method of attack that involves the exploitation of vulnerabilities inside a system's backend database. This attack vector employs hostile entities, typically in the form of SQL codes, to manipulate the database and extract unauthorized data that was not intended to be disclosed. This type of database may include several elements, such as banking credentials, sensitive client information, confidential company data, and user lists.
What are application attacks?
One particular kind of cyberattack that tries to change the database connected to the targeted web application is called an application attack. Database preservation and the security of related online applications can be accomplished through the implementation of a wide range of techniques, tactics, and frameworks that are offered by a reliable web application security course, like the one offered by Bytecode Security.
What is meant by Web security?
Web security refers to the set of security techniques and criteria employed by an earnest information security professional to protect web applications. This aspect holds significant importance within the field of cyber security, as it involves the execution of various cyber attacks targeting websites and web-based applications to illicitly acquire their sensitive and critical datasets.
What is Web security requirements?
The primary and notable requirements for web security are outlined as follows:
- Authentication,
- Authorization,
- Data Protection, and
- Nonrepudiation
What is Owasp certification?
Established in 2001, the Open Web Application Security Project (OWASP) offers free security tools and resources to help organizations protect critical apps. Cybrary's OWASP certification training course covers the organization's popular “Top 10” risk assessment.
What is Owasp used for?
The Open Web Application Security Project (OWASP) is a non-profit organization founded in 2001, with the goal of helping website owners and security experts protect web applications from cyber attacks. OWASP has 32,000 volunteers around the world who perform security assessments and research.
Is Cyber Security hard?
Yes, the field of cyber security encompasses a comprehensive curriculum consisting of twelve distinct courses, each demanding a substantial amount of rigorous academic inquiry. Therefore, the workload associated with these courses might occasionally induce a certain level of stress. The field of cyber security offers a wide range of employment opportunities that are accompanied by lucrative compensation, so it serves as a compelling incentive for individuals to pursue a career in this domain.
To do an extensive 1 Year Diploma in Cyber Security Course by Bytecode Security under the primetime guidance of highly skilled training professionals, call +91-9513805401 now.
Are Web Apps Safe?
In the realm of technology, it is widely acknowledged that achieving complete security is an elusive goal. However, it is plausible to enhance the protection of web applications by engaging the expertise of a competent web application security professional. Individuals with a strong inclination towards acquiring knowledge about the diverse protocols related to web application security may choose to enroll in the web application security course offered at the esteemed facilities of Bytecode Security.
What is web security and its types?
Web security refers to the systematic measures used by information security experts to ensure the confidentiality of information pertaining to web applications. Web application security encompasses several components such as databases, software, applications, servers, and devices in a comprehensive manner.
What are 7 types of security threats?
Seven primary categories of security threats are commonly recognized. These categories encompass a range of potential risks and vulnerabilities that might compromise the security of a system or network.
- Malware
- Emotet
- Denial of service
- Man in the middle
- phishing
- SQL injection
- Password attack
How do websites get hacked?
Typically, a website is compromised when an individual with malicious intent identifies concealed weaknesses within the security infrastructure of a web application and endeavors to exploit these flaws through diverse techniques. Website hacks typically fall into three distinct kinds, namely:
- Access Control,
- Software vulnerabilities, and
- Third-party integrations/ services.
Which is an example of a Web security threat?
Web security dangers include, but are not limited to, malware, data breaches, DoS attacks, and multiple avenues of attack.