The Ethical Hacking Course in Delhi is offered to hacking aspirants globally. This course is specially designed to introduce students to the fundamentals of hacking techniques, objectives, and tools. Such skills are possessed by professionals to take on the plans to handle online and offline data security measures.
Adversaries are becoming more ruthless. They don’t know when to stop and keep devastating everything that comes their way of breaching data. Let’s know what Ethical Hacking is and what the Ethical Hacking Course in Delhi is offered to students of ethical hacking.
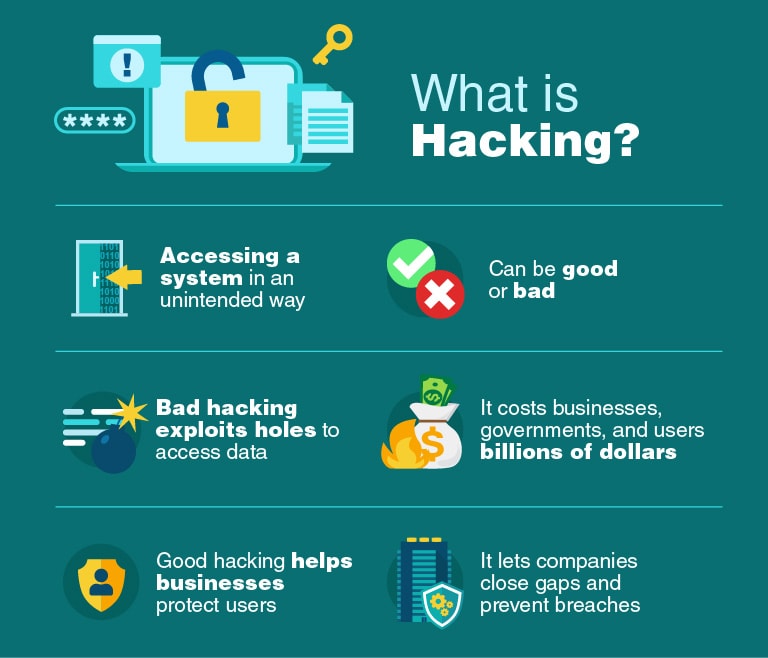
What is Ethical Hacking?
Ethical Hacking is the skillsets of hacking techniques and tools which can help hackers to perform hacking with legitimate attacks. These techniques help organizations to know their limits in data security measures.
If websites show vulnerable points during penetration testing, it means that it needs a concentration of professionals to enhance the security of the websites. Malicious hackers are ready to hack your systems, and you need to enhance the security there before the adversaries can penetrate those.
Difficulty in saving your data is that you neglect to enhance your security measures until you become a part of the victims of the events happening each year with many hacked systems. You need to fix the bugs before the hackers can reach them. Otherwise, you know the consequences.
Types of Ethical Hacking?
1. Black-Box Testing
When an attacker doesn’t have a single clue about the system, he/ she uses Black-Box Testing. They test the software from outside the device via brute force attack. There are two things you need to know whenever you want to test a website’s vulnerability, and those are
- Computing Language is used to make the website.
You can estimate that this testing technique can create a big amount of Chaos, and it’s one of the most dangerous types of hacking in cyber security. This technique helps in identifying security loopholes in a network/ system that can exploit at any second. Via such techniques, sensitive data such as credit card numbers and bank accounts can be sold for personal and intentional causes. Sometimes these can be used for identity theft or fraud.
2. White-Box Testing
In this technique, a hacker knows how the system works and its loopholes, even before he/ she tries to exploit the system. This kind of testing is a practice that is often done by developers so they can know how well the system is working in their habitat environment. Hackers try to break into the system.
They are bounded by contracts with Company Policy and work under IT Departments. This gives them the legal authority to check systems’ vulnerabilities before getting to work. Ex – Designing Reviews, Code Inspections, Data-Flow Analysis, and Statement Coverage.
3. Gray-Box Testing
You can expect it like a duo of White-Box and Black-Box Testing. Adversaries do have a bit of a clue about the system, but not fully. That’s why they are dependent on reasoning skills and technical knowledge to find out loopholes within the system or network.
Their working nature can change due to the change in working environments. Sometimes they can be involved in good purpose, and sometimes that could be malicious. Ex- Money Loot, and they could use computer viruses to get access. Unwilling but can become black hat hackers.
Areas that can be tested are as follows:
- Usability Tests
- Performance Tests,
- Security Tests.
1. Web Application Hacking
You know that any workable application on web platforms is known as a Web Application. In Web Application Hacking, you learn to exploit security vulnerabilities in web-based applications. These applications are created via the following computing languages:
- HTML
- CSS
- JavaScript
- PHP,
- Ruby on Rails.
If you want to know how computing languages and web browsers impact web applications without performing an act or getting authorized, you can use this technique. Ex – cross-site scripting (XSS), which involves malicious code into a website’s HTML.
If you successfully accomplish an XSS Attack, you’ll be able to hack browsers’ session with the server without using any username or password.
2. Hacking Wireless Networks
In this hacking technique, hackers access a computer network without authorization, usually by exploiting the system’s security loopholes. Ex – wardriving,
This is a technique in which a person rolls around via vehicle in an area to look for open Wi-Fi Networks. With this, you’ll be able to find unprotected/ poorly protected networks.
3.Social Engineering
This is one of the most popular techniques that hackers use for data collection of systems from various sources. Via three types of social engineering, data can be gathered, and are
- Human-Based
- Mobile-Based
- Computer-Based
Due to a lack of security policies and hardware/software tools to protect systems from social engineering attacks; they can’t be detected.
4.Web Server Hacking
Server Platforms give space for those Web Content as a Software Application. Due to this, adversaries have the upper hand over stealing sensitive information, passwords, and business data via DoS Attacks, Port Scans, SYN Floods, and Sniffing. Web Servers are attacked by adversaries to get monetary benefits from theft, sabotage, blackmail, and extortion.
What are the key concepts of Ethical Hacking?
Following are the key concepts of Ethical Hacking:
1.Scanning
Once you start the feature scanning, you get the target’s network, its devices, and present configurations. These will feed your next process, which is finding the loopholes, after which you can attack the device according to the weakest point found by the process of finding vulnerabilities.
2. Enumeration
In this step, you gather the data about the targeted network, like – usernames, and passwords, that can be used in the post levels of hacking.
3. Exploitation
This step teaches you ways to penetrate the weakest point of the targeted machine/ devices.
What are the Roles and Responsibilities of an Ethical Hacker?
The roles and responsibilities of an ethical hacker are to secure the contracted organization’s systems, networks, and software from unknown online threats that are becoming more ‘n’ more dangerous for the organizational environment.
Which course is Best for Ethical Hacking in Delhi?
The Best Ethical Hacking Course in Delhi is offered by Bytecode Security, which has introduced a total number of 20 concepts that are mentioned below.
<modules>
Difference Between CEH v11 vs CEH v12?
| Basis | CEH V11 | CEH V12 |
| Total Number of Modules | 20 | 20 |
| Total Number of Slides | 1640 | 1676 |
| Total Number of Labs | 200 | 220 |
| Total Number of New Labs | 92 | 33 |
| Attack Techniques | 420 | 519
MITRE ATT&CK Framework, Diamond Model of Intrusion |
| New Technology Added | OT Technology, Serverless Computing, WPA3 Encryption, APT, Fileless Malware, Web API, and Web Shell | Analysis, Techniques for Establishing Persistence, Evading NAC and Endpoint Security, Fog Computing, and Grid Computing |
| OS Used for Labs | Windows 10, Windows Server, Windows 11, Windows Server 2019, Parrot Security, Android, Ubuntu Linux | Windows 10, Windows Server 2022, Windows Server 2019, Parrot Security, Android, Ubuntu Linux |
| Exam | 125 Questions (MCO) | 125 Questions (MCO) |
| Exam Duration | 4 Hours | 4 Hours |
| Exam Delivery | VUE/ ECCEXAM | VUE/ ECCEXAM |
| Compliance | Final NICE 2.0 Framework | Final NICE 2.0 Framework |
Ethical Hacking Course Overview
The Ethical Hacking Course in Delhi offered by Bytecode Security is introducing several amazing concepts that are as follows:
| S.No. | Key Features | S.No. | Key Features |
| 1. | Introduction to Basics of Ethical Hacking | 5. | Web Session Hijacking |
| 2. | In-depth Networks Scanning | 6. | Viruses and Worms, Trojan and Back door, SQL Injection Manual Testing |
| 3. | System Hacking Password Cracking & Bypassing | 7. | Hacking Webservers Server Rooting, Hacking Wireless Network, Penetration Testing: Basics |
| 4. | Mobile Hacking | 8. | Internet of Things (IoT) Hacking, Cloud Security, and many more. |
How to get CEH Certification?
If you want a CEH Certification, you need to contact a reputed institute that is offering this certification which should be valid wherever you go for a job profile that you want or that you can acquire after completing your course.
For that, you can get in contact with Bytecode Security, which has a very long way of experience with the Ethical Hacking Course in Delhi. Several students have already been certified with their certifications, and the certification is valid in most MNCs.
The reason behind that is organizations need certified professionals to tell them where they need an enhancement in their security patches to get secured from unknown threats. CEH Certification certifies a person to be a professional, ethical hacker. So, why don’t you go for it? It is valid in several MNCs.
Best Institute for Ethical Hacking Certification in Delhi.
Now that you know what ethical hacking is, you need the best institute for Ethical Hacking Certification in Delhi. Where could you get the best trainers to train you with the latest techniques and tools?
For that, you can rely on Bytecode Security, which has been working in the field of ethical hacking for a long time with professionals of ethical hacking. With that, they also have introduced the latest CEH v12 Training in Delhi.
This course is now introducing the aspirants to several new and amazing concepts of ethical hacking, which you’ll be able to know about in this course offered by Bytecode Security. To know more about it, you can contact Bytecode Security.
Duration of the Diploma Course of Ethical Hacking Training in Delhi?
The duration of the Ethical Hacking Course in Delhi is 60 hours.
Course Fees in Ethical Hacking Training Institutes in Delhi?
Ethical Hacking Course in Delhi Fees will totally fit your budget. Several institutes are offering this course to the aspirants while keeping the rates higher than the actual student can afford. However, contacting Bytecode Security will give them a chance to learn the skills on a very pocket-friendly budget which will allow them to fulfill their dream of choosing a career line in which they would be able to prove their potential through many practices during the sessions. What are you waiting for? Get in touch with Bytecode Security.
Frequently Asked Questions:
About Ethical Hacking Course In Delhi| Ethical Hacking Certification
1.Can I Take Ceh v12 Course & Exam Online?
Yes! CEH v12 Course & Exam is available Online in both Instructor Led self-paced learning and live Instructor-led modes. However, Bytecode is offering Online Ethical Hacking Course in Delhi for the student of hacking with the updation of techniques and tools every year.
This is going to be one of the most amazing experiences for the students that are preparing to start a career in hacking and so on. Bytecode has intently proposed this course to deliver quality education for the youth, and not only them but the elders who are optimistic about learning something new about the world can do it without thinking about the boundaries.
2. Can I Do Ethical Hacking Course After 12th Class?
Well, several institutes might say that you must have an undergraduate degree before approaching such career options training. However, Bytecode starts from the degree from which the student can pick the pace and go with the flow. Ethical hacking is one of the fastest-growing educational-oriented career options.
If you get the professionals to train you, you’ll experience something new with the proper guidance. Bytecode offers Ethical Hacking Course in Delhi, which seems to be very deeper in explaining the fundamental concepts related to hacking. What are you waiting for? Contact Now!
3. How much does Ethical Hacking Certification training cost?
Well, every other institute is trying to provide this course at a high price where their training syllabi are not well-versed. In the end, they end up getting fed from learning new skills. There, Bytecode focuses more on a better and deeper understanding of concepts with the fundamental concepts, including the latest techniques and tools.
Moreover, here the students get this course at pocket-friendly rates. What are you waiting for? Enroll, Now!
4. What is salary of ethical hacker?
Several job profiles are there in the Ethical Hacking Career Lane. Moreover, according to those profiles, salary packages can differ that are as follows:
- Information Security Analyst. – ₹3.5 Lakhs – ₹12.0 Lakhs/ Annual
- Security Analyst. – ₹5.1 Lakh/ Annual
- Certified Ethical Hacker (CEH) – ₹5.02 Lakh/ Annual
- Security Consultant (Computing / Networking / Information Technology) – ₹5.8 Lakhs – ₹24.0 Lakhs/ Annual
- Information Security Manager. – ₹17 Lakh/ Annual
- Penetration Tester – ₹2.0 Lakhs – ₹25.8 Lakhs/ Annual
5. What do certified ethical hacker do?
They work professionally for high-end organizations to provide them with the utmost security from unknown threats out there involving adversaries. Online hackers are confident enough to penetrate any system, network, or device to steal data from that.
A Certified Ethical Hacker knows the ways an unethical hacker could perceive to get into the database of the organization to do his work. Ethical hackers possess several amazing tools to enhance the security of networks and devices.
So, it can be a perfect career option for several aspirants who have been looking for a reputed career line.
6. Which language is best for Ethical Hacking?
Well, as for ethical hacking, you must have the knowledge of coding, and for that, you must have the skillset knowledge of computing languages. One of the most popular computing languages is Python Programming Language.
This language is one of the easiest computing languages that a beginner can choose to start learning ethical hacking. Do you want to know why? Ask professionals! Bytecode Security!
7. What should I study to become a hacker?
Well, there’s nothing that you can do without having knowledge of the actual procedures of the work. That, the hacking line is one of the professional career-making opportunities where you can perform several tasks to profit the organizations on the basis of online and offline security of data.
Hacker doesn’t stop learning at any age in life. That’s why they do possess a greater bank of knowledge to process practices. To learn such skills, you can ask professionals.
8. What skills do you need to be an Ethical Hacker?
If you want to work as a professional, ethical hacker, you should have the following skillsets so you can practice with the latest techniques and tools on various systems of organizations.
- Networking Skills.
- Computer Skills.
- Linux Skills.
- Programming Skills.
- SQL Skills.
- Hardware Knowledge.
- Knowledge of Reverse Engineering.
As you can see that there are a lot of things that you should consider before applying for a job in any company, you need a piece of evidence to prove that you have mastered the skills mentioned.
For that, you can join a course that offers an introduction to Ethical Hacking Course. The Ethical Hacking Course in Delhi offered by Bytecode Security would be the best option for you to choose right now.
That’s because it is customized by professionals for the aspirants of ethical hacking under severe determination.
9. Is there any job for hackers?
There are several job profiles that a hacker can apply for after completing the course and certifications with CEH v12, and those are as follows:
- Mid-level Information Assurance Security Audit
- Cybersecurity Auditor
- Security Administrator
- IT Security Administrator
- Cyber Défense Analyst
- Vulnerability Assessment Analyst
- Warning Analyst
- Information Security Analyst 1
- Security Analyst L1
- Infosec Security Administrator
- Cybersecurity Analyst L1, L2, & L3
- Network Security Engineer
- SOC Security Analyst
- Security Analyst
- Network Engineer
- Senior Security Consultant
- Information Security Manager
- Senior SOC Analyst
- Jr Penetration Tester
- Solution Architect
- Cybersecurity Consultant
- Security Compliance Analyst
10. Which course is best for ethical hacking?
The best course that you can choose for ethical hacking is the Ethical Hacking Course in Delhi offered by Bytecode Security which introduces the students to the fundamental concepts of hacking techniques, their objectives, and tools related to hacking in a deeper and more meaningful way.
Bytecode Security has been offering this course in Delhi for the aspirants of hacking. Several organizations have already manifested themselves in learning ethical hacking skills to maintain their quality security measures.
Thus, learning these skills would be beneficial for you, and you can join the Ethical Hacking Course in Delhi offered by Bytecode Security. For more information, you can get in contact with Bytecode Security.